There are two phases in this : Growing phase − all the locks are issued in this phase.
, It uses the only exclusive lock. A binary lock has only two states:
 PPT Transactions PowerPoint Presentation, free download ID7190 From slideserve.com
PPT Transactions PowerPoint Presentation, free download ID7190 From slideserve.com
The locks provide a method for securing the data that is being used so no. Locks in dbms help synchronize access to the database items by concurrent transactions. Growing phase − all the locks are issued in this phase. The lock table can contain the following types of locks.
PPT Transactions PowerPoint Presentation, free download ID7190 I misread this as what is a lock in a database not what is a database lock.
Review this section for details about lock management considerations that can help you to maximize the. There are two types of locks. Unlike binary locks, read/write locks may be set to 3 values, i.e., shared, exclusive or unlocked. There are four types of lock protocols available:
 Source: chegg.com
Source: chegg.com
An intention lock is something when a lower granularity object needs a lock and then the lock manager places a lock on the higher granularity object. In dbms, the lock is a mechanism used for validating data integrity. Growing phase − all the locks are issued in this phase. Every transaction will lock and unlock the data item in two different phases. Solved 1. Compare Binary Locks To Exclusive/shared Locks…..
 Source: slideserve.com
Source: slideserve.com
Locking mechanisms are a way for databases to produce sequential data output without the sequential steps. Locked (1) or unlocked (0). There are two phases in this : Click on the arrow beside blocking sessions to display “blocking. PPT Describing and storing data in a DBMS PowerPoint Presentation.
 Source: documents.pub
Source: documents.pub
If an object—that is, a database, table, page, or row—is locked by a transaction, no. The locking in a database can be done at 4 levels, which start with the database at the highest level and down via table and page to the row at the. There are two phases in this : Every transaction will lock and unlock the data item in two different phases. Slide 1 Lecture 7 Concurrency Control and Recovery Transactions, ACID.
 Source: digitalnoteshub.com
Source: digitalnoteshub.com
Reduce lock footprint of expensive queries by doing performance tuning and making them efficient. It is also known as a read. In oracle, the engine locks j table data automatically while executing. Locking mechanisms are a way for databases to produce sequential data output without the sequential steps. Concurrency Control In DBMS(2 Phase Locking And Timestamp Ordering.
 Source: slideserve.com
Source: slideserve.com
It uses the only exclusive lock. An intention lock is something when a lower granularity object needs a lock and then the lock manager places a lock on the higher granularity object. Lock identifiers are used to enable applications to coordinate their use of. They are also known as read/write locks. PPT Chapter 16 Concurrency Control PowerPoint Presentation, free.
 Source: slideserve.com
Source: slideserve.com
There are two types of locks. The locking in a database can be done at 4 levels, which start with the database at the highest level and down via table and page to the row at the. For the latter question, i am not sure as the concept of a lock in dbms’ is usually about tables… — let’s. Lock identifiers are used to enable applications to coordinate their use of. PPT Describing and storing data in a DBMS PowerPoint Presentation.
 Source: educba.com
Source: educba.com
It is the simplest way of locking the data while transaction. This protocol requires that locking should be two phase and all executive mode locks taken by a transaction should be held until the transaction. Then, find “performance” and click on the arrow adjacent to it. The dbms will choose one of the processes to abort and roll back so the other process can continue. Lock Based Protocols in DBMS Learn the Types of Locks in DBMS.
 Source: slideserve.com
Source: slideserve.com
Unlike binary locks, read/write locks may be set to 3 values, i.e., shared, exclusive or unlocked. For the latter question, i am not sure as the concept of a lock in dbms’ is usually about tables… — let’s. A binary lock has only two states: This procedure allocates a unique lock identifier (in the range of 1073741824 to 1999999999) given a lock name. PPT Describing and storing data in a DBMS PowerPoint Presentation.
 Source: documents.pub
Source: documents.pub
Timeout is part of types of locking. Unlike binary locks, read/write locks may be set to 3 values, i.e., shared, exclusive or unlocked. When locks are held too long,. Locks in dbms help synchronize access to the database items by concurrent transactions. Slide 1 Lecture 7 Concurrency Control and Recovery Transactions, ACID.
 Source: fymca2020-g12.blogspot.com
Source: fymca2020-g12.blogspot.com
Strict two phase locking protocol: The first lock can be acquired on any data item. Most rdbms systems offer the following lock types: This procedure allocates a unique lock identifier (in the range of 1073741824 to 1999999999) given a lock name. Concurrency Control Protocols in DBMS.
 Source: slideserve.com
Source: slideserve.com
The lock table can contain the following types of locks. Locking mechanisms are a way for databases to produce sequential data output without the sequential steps. There are four types of lock protocols available: The dbms will choose one of the processes to abort and roll back so the other process can continue. PPT Transactions PowerPoint Presentation, free download ID7190.
 Source: rdbmsql.com
Source: rdbmsql.com
A transaction, as explained earlier, can contain multiple. There are two phases in this : Locks in dbms help synchronize access to the database items by concurrent transactions. For the latter question, i am not sure as the concept of a lock in dbms’ is usually about tables… — let’s. What is DBMS Advanced SQL Server (RDBMS).
 Source: slideserve.com
Source: slideserve.com
A binary lock has only two states: There are different types of locks. Locks in dbms help synchronize access to the database items by concurrent transactions. Unlike binary locks, read/write locks may be set to 3 values, i.e., shared, exclusive or unlocked. PPT Data and Applications Security Developments and Directions.
 Source: slideserve.com
Source: slideserve.com
Lock identifiers are used to enable applications to coordinate their use of. The locking and unlocking of data items in lock based protocols in dbms are implemented in 2 modes: Then, find “performance” and click on the arrow adjacent to it. There are two phases in this : PPT Fresher Training Program Relational Database Management System.
 Source: slideserve.com
Source: slideserve.com
An intention lock is something when a lower granularity object needs a lock and then the lock manager places a lock on the higher granularity object. A binary lock has only two states: In dbms, the lock is a mechanism used for validating data integrity. An intent lock can be an intent shared (is), intent exclusive (ix), or intent shared. PPT Fresher Training Program Relational Database Management System.
 Source: fymca2020-g12.blogspot.com
Source: fymca2020-g12.blogspot.com
There are different types of locks. The locking in a database can be done at 4 levels, which start with the database at the highest level and down via table and page to the row at the. Hence, our lock, i.e., lock (x), may. I misread this as what is a lock in a database not what is a database lock. Concurrency Control Protocols in DBMS.
 Source: documents.pub
Source: documents.pub
Click on the arrow beside blocking sessions to display “blocking. Lock management is one of the factors that affect application performance. Subsequent locks are allowed only if the parent is. I misread this as what is a lock in a database not what is a database lock. Slide 1 Lecture 7 Concurrency Control and Recovery Transactions, ACID.
 Source: slideshare.net
Source: slideshare.net
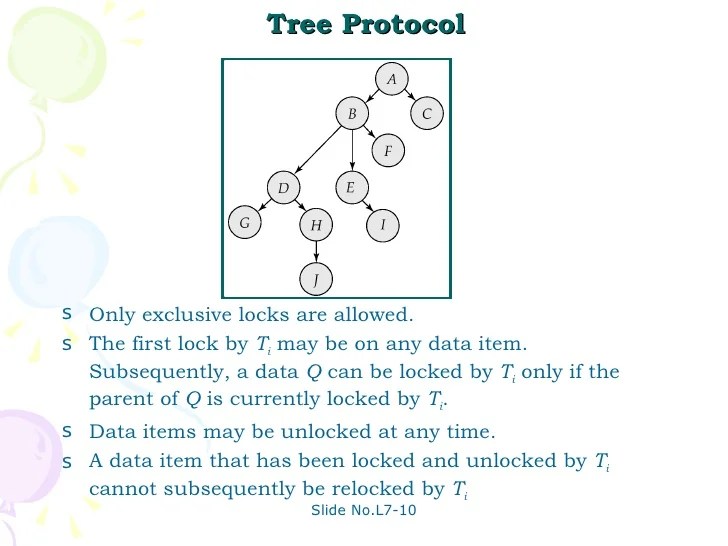
There are two phases in this : The first lock can be acquired on any data item. There are two types of locks. An intent lock can be an intent shared (is), intent exclusive (ix), or intent shared. Unit06 dbms.
 Source: documents.pub
Source: documents.pub
It is the simplest way of locking the data while transaction. There are four types of lock protocols available: Hence, our lock, i.e., lock (x), may. Most rdbms systems offer the following lock types: Slide 1 Lecture 7 Concurrency Control and Recovery Transactions, ACID.
 Source: documents.pub
Source: documents.pub
Levels of locking in dbms. Locking mechanisms are a way for databases to produce sequential data output without the sequential steps. There are different types of locks. The dbms will choose one of the processes to abort and roll back so the other process can continue. Slide 1 Lecture 7 Concurrency Control and Recovery Transactions, ACID.
 Source: documents.pub
Source: documents.pub
When locks are held too long,. There are four types of lock protocols available: This procedure allocates a unique lock identifier (in the range of 1073741824 to 1999999999) given a lock name. Locked (1) or unlocked (0). Slide 1 Lecture 7 Concurrency Control and Recovery Transactions, ACID.
 Source: slideserve.com
Source: slideserve.com
A transaction in any system implementing lock based concurrency control cannot read or write a statement until it has obtained the required locks. The lock table can contain the following types of locks. For the latter question, i am not sure as the concept of a lock in dbms’ is usually about tables… — let’s. There are different types of locks. PPT Topics in Database Administration PowerPoint Presentation, free.
 Source: slideserve.com
Source: slideserve.com
They are also known as read/write locks. Underneath it, you will find “blocking session”. Hence, our lock, i.e., lock (x), may. The lock table can contain the following types of locks. PPT Topics in Database Administration PowerPoint Presentation, free.
 Source: slideserve.com
Source: slideserve.com
The locking and unlocking of data items in lock based protocols in dbms are implemented in 2 modes: It uses the only exclusive lock. Reduce lock footprint of expensive queries by doing performance tuning and making them efficient. Then, find “performance” and click on the arrow adjacent to it. PPT Database Systems Design, Implementation, and Management Tenth.
 Source: slideserve.com
Source: slideserve.com
Then, find “performance” and click on the arrow adjacent to it. When locks are held too long,. It is the simplest way of locking the data while transaction. It uses the only exclusive lock. PPT Chapter 16 Concurrency Control PowerPoint Presentation, free.
Locked (1) Or Unlocked (0).
It is also known as a read. Subsequent locks are allowed only if the parent is. When locks are held too long,. Locking mechanisms are a way for databases to produce sequential data output without the sequential steps.
Timeout Is Part Of Types Of Locking.
The first lock can be acquired on any data item. Levels of locking in dbms. A transaction, as explained earlier, can contain multiple. Unlike binary locks, read/write locks may be set to 3 values, i.e., shared, exclusive or unlocked.
Review This Section For Details About Lock Management Considerations That Can Help You To Maximize The.
Lock identifiers are used to enable applications to coordinate their use of. A binary lock has only two states: Hence, our lock, i.e., lock (x), may. A transaction in any system implementing lock based concurrency control cannot read or write a statement until it has obtained the required locks.
The Locking And Unlocking Of Data Items In Lock Based Protocols In Dbms Are Implemented In 2 Modes:
It uses the only exclusive lock. The dbms will choose one of the processes to abort and roll back so the other process can continue. It is the simplest way of locking the data while transaction. If a data item is locked, then it cannot be accessed by other transactions i.e., other transactions are forced to wait until the lock is released by the previous.







